10 Simple Techniques For Risk Management Enterprise
Risk Management Enterprise for Beginners
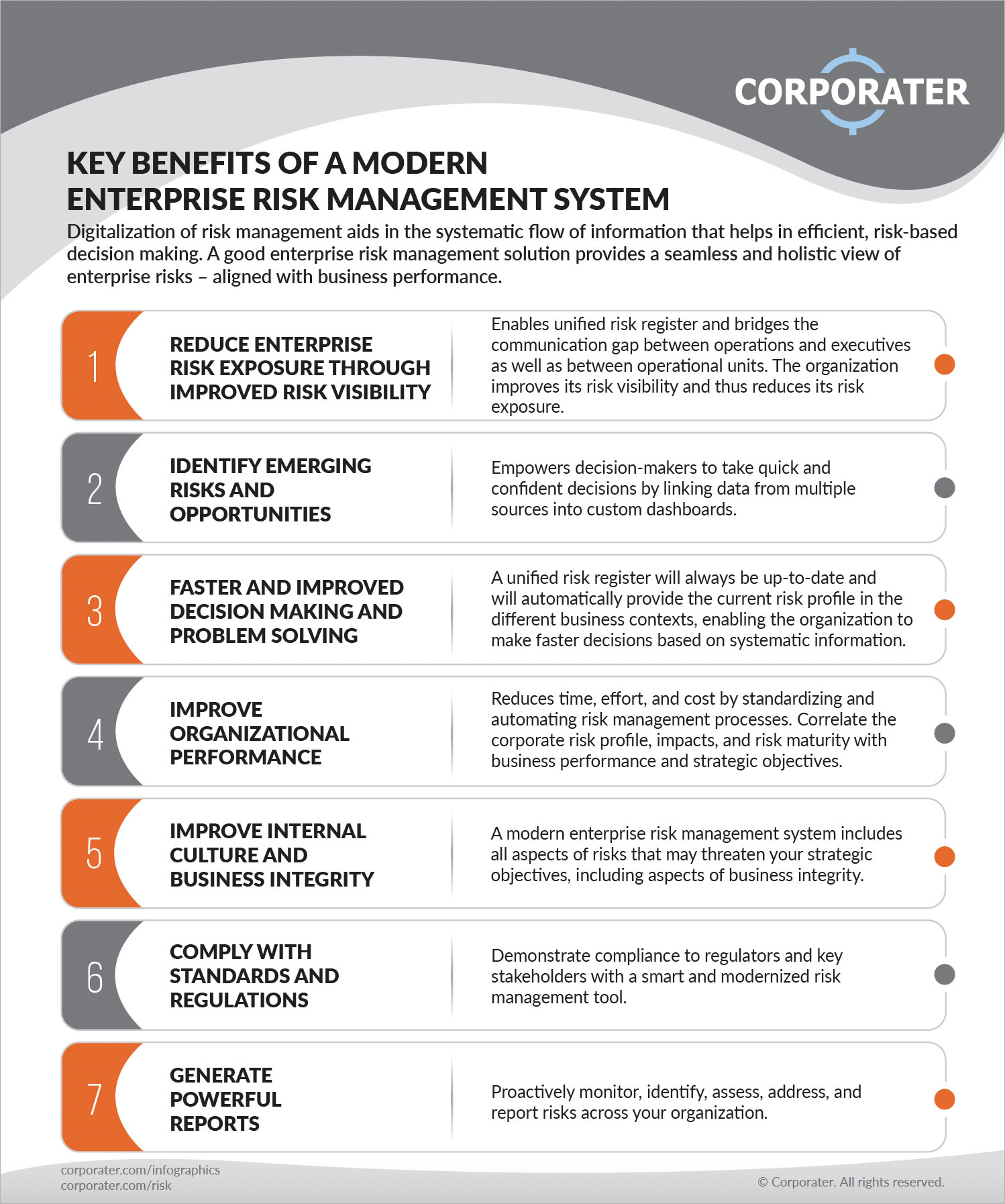
Table of ContentsRisk Management Enterprise Fundamentals ExplainedThe Definitive Guide to Risk Management EnterpriseThe Facts About Risk Management Enterprise Revealed
Control that can view or modify these elements by setting specific access rights for private users, making sure information safety and security and customized usability. Allows users to tailor their interface by choosing and organizing necessary information aspects. Provides a personalized experience by allowing customization of where and exactly how data aspects are shown.It allows accessibility to real-time incorporated data quickly. Risk Management Enterprise. This assists remove squandered time on hands-on record collection. Also, centers can use extensive data knowledge for quicker and extra informed decision-making. It allows the automatic production of stakeholder records for people or teams. Allows timely decision-making and reduces delays caused by outdated information.

Diligent is a risk monitoring software that permits maximizing efficiency, and enhances growth. It additionally assists monitor dangers with ERM software that consists of incorporated analytics and adapts to your company requirements.
The 6-Second Trick For Risk Management Enterprise
Streamlines the process of collecting danger data from numerous parts of the organization. Gives management and the board with real-time risk insights. Use ACL's innovative analytics to detect threat patterns and anticipate threats.
This permits firms to catch risk insights and red flags in the third-party vendor's safety and security report. Makes it possible for business to capture and document threat insights and red flags in third-party vendor safety and security records.
Recognizing dangers beforehand helps a facility plan for audits. It additionally lowers risk with streamlined compliance and risk management. As a result of this centers will not have to manage different systems for threat tracking. helpful hints The customers of Hyperproof can streamline risk management in one area. It can aid accumulate and track all your dangers in the Hyperproof threat register.
It offers quick accessibility to needed info and documents. This guarantees the security of Hyper proof circumstances by making it possible for multi-factor authentication (MFA) utilizing authenticator applications such as Google Authenticator, Microsoft Authenticator, or Authy.
An Unbiased View of Risk Management Enterprise

It provides top-tier security attributes to protect sensitive data. This threat monitoring software program is a perfect tool for centers looking to deal with unnecessary concerns or risks.
Individuals can also utilize the AI-powered devices read here and pre-existing web content to develop, assess, prioritize, and address threats effectively. Enhances the procedure of setting up and inhabiting threat registers. Uses AI and collection content to boost threat analysis precision. It makes it possible for much faster recognition and reduction of threats, This is mostly a visual model.